KDH: Kerberos5 with Perfect Forward Secrecy
This site reflects work in progress.
Read the specification (submitted as an IETF formal Internet Draft specification)
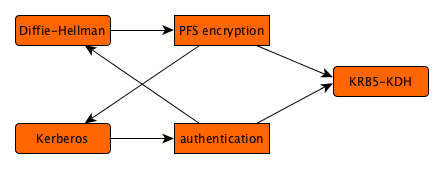
As discussed on the introduction page, Kerberos5 is an attractive authentication solution with somewhat weak encryption properties, whereas Diffie-Hellman is an attractive encryption solution without authentication properties. When the two can be cryptographically bound together, their powers enhance each other, and we can have the best of both worlds.
This page describes a general extension for Kerberos5 that makes it support this cryptographically bound combination of algorithms. It has very little impact and offers absolute certainty of how to act. Furhtermore, its code can be hidden behind the GSS-API, and simply act as an extra security measure that the Kerberos5 implementation of that API can offer.
The conceptual protocol describes a method of achieving this cryptographic binding. This is almost literally translated into this specification. Another translation into TLS is not as direct, but it is stronly related.
Passing the Diffie-Hellman key exchange can be done through a subkey in the authenticators to AP-REQ and AP-REP messages; this subkey is meant to pass a replacement for the session key that is shared by the KDC. We defined a format for sharing Diffie-Hellman key exchange in this field, and prescribe its use. There is no reason why this cannot integrate with realm crossover mechanisms, although the usual security considerations apply, and it should be noted that these are not mitigated by using KDH.
Summary of changes
Changes to Kerberos5:
- A new encryption type for a Diffie-Hellman key exchange message;
- A new Kerberos5 ticket flag to indicate support for the Diffie-Hellman encryption type.
